Solana Passkeys: The Future of Crypto Wallet UX
Originally published on the Helius blog
1) Passkeys enable passwordless, seedless Solana wallet onboarding via secure, device-bound sessions. Since WebAuthn passkeys use P-256 (incompatible with signing transactions on Solana’s Ed25519), they can’t sign transactions directly.
2) Para solves this by using passkeys for session authorization, unlocking a secure MPC-managed Ed25519 signer. The result: instant onboarding, persistent sessions, and Solana-native signing with no extensions or recovery phrases needed.
Powering Passwordless Apps
Solana apps need to deliver crypto wallet onboarding that’s fast, secure, and native. Wallets such as Phantom have led the way, but still require users to manage seed phrases.
Passkeys change that.
Built on the WebAuthn standard and FIDO2 protocol, passkeys enable biometric or hardware-based login (e.g., Face ID, Touch ID, Windows Hello, or YubiKeys) without storing or exposing private keys.
Passkeys replace traditional passwords by using a cryptographic key pair where the private key stays on the user’s device in a secure hardware module, and only the public key is shared.
While most apps use passkeys to replace passwords with passwordless authentication, Para takes a different approach, using passkeys as cryptographic authorization to establish secure wallet sessions.
No passwords. No seed phrases. Just cryptographic access built into the user’s device to provide a simplified user experience.
With SIMD-0075 live on Mainnet, Solana can now verify passkeys.
— Helius (@heliuslabs) June 24, 2025
Passkeys are a huge unlock for onboarding and UX:
Wallets can now support biometric signing, passkey-enabled 2FA, and bring more robust wallet UX to Solana.
Learn how to get started with @get_para 👇 pic.twitter.com/YPFgjNDnXG
Original post on the Helius blog
Why do passkeys matter for Solana wallet UX?
When paired with Para’s embedded wallet SDK, passkeys unlock:
- Instant onboarding: no installs or seed phrases
- Secure key management: keys stay device-bound and phishing-resistant
- Persistent sessions: users stay connected across visits and devices
What happens when users register a new Para passkey?
The client (browser or OS-level credential manager) creates a key pair:
- The private key is stored in the device’s secure enclave (e.g., Trusted Platform Module, Secure Enclave, or Android Keystore)
- The public key and credential metadata are sent to the server
Passkey metadata includes:
- Credential ID (unique to each passkey)
- Challenge nonce
- RP ID (your app's domain)
- Cryptographic algorithm (usually P-256)
Passkeys on Solana: Solving the Signature Mismatch
Most WebAuthn authentication defaults to the P-256 curve (secp256r1), a widely used elliptic curve designed for broad compatibility across browsers and devices. The P-256 curve is great for general-purpose web login, but not for Solana. That’s because Solana uses a different curve, Ed25519 (based on Curve25519), which is optimized for fast, deterministic signatures and high-throughput validation via SIMD (Single Instruction, Multiple Data) instructions.
This mismatch matters: P‑256 and Ed25519 aren’t directly compatible. WebAuthn passkeys today can’t generate Ed25519 signatures, and browsers don’t expose APIs for Ed25519 signing through secure enclaves. As a result, passkeys can't directly sign Solana transactions.
That gap made passkey support on Solana a technical hurdle. SIMD-0075: Secp256r1 Precompile, approved in May 2024, reaffirmed Ed25519 as Solana’s preferred curve, citing benefits like deterministic signing (no nonce risk), SIMD vectorization, and ecosystem interoperability.
In June 2025, Solana enabled native on-chain verification of secp256r1 (P-256) signatures via a new precompile, allowing apps to verify passkey signatures on-chain (e.g., to confirm user login or identity proofs). However, Solana transactions still require Ed25519 signatures, which WebAuthn passkeys can’t produce. That means passkeys alone still aren’t sufficient for wallet-level signing. To make passkeys work for transaction signing, you’d still need an additional wrapper layer (similar to how ERC‑4337 bundlers work on Ethereum) to transform a passkey-based action into an Ed25519-compatible transaction.
That’s where our infrastructure comes in:
- Instead of using passkeys to sign transactions, we use them as an authorization primitive
- The passkey unlocks a scoped session
- This session grants access to an Ed25519-compatible signing key managed by Para’s MPC (Multi-Party Computation) infrastructure
This design bypasses the curve mismatch while delivering:
- Full Solana compatibility
- Fast, native onboarding with passkeys
- Secure self-custody and MPC-based key management
For a deeper dive into curve trade-offs or zero-knowledge proofs, check out this primer on elliptic curves and zero-knowledge.
Para Passkeys: Authorization, Not Just Authentication
We introduced passkey-based session authorization in 2023, a core component of the Para embedded wallet SDK. Instead of treating passkeys as just a login method, we use them to control access to wallet operations securely.
In Para’s SDK, passkeys are used to authorize wallet sessions after the user has logged in (via OAuth, email/password, etc). This separation of concerns—auth for identity, passkeys for wallet access—creates a more secure foundation for Para universal embedded wallets.
When a user creates a wallet with Para, a passkey is registered and tied to their device.
Specifically, it:
- Signs an authorization challenge
- Confirms the user controls the device and wallet
- Establishes a scoped, signed session that can be persisted
This session then unlocks sensitive operations like:
- Sending transactions
- Accessing encrypted, session-bound keys
- Approving smart contract interactions
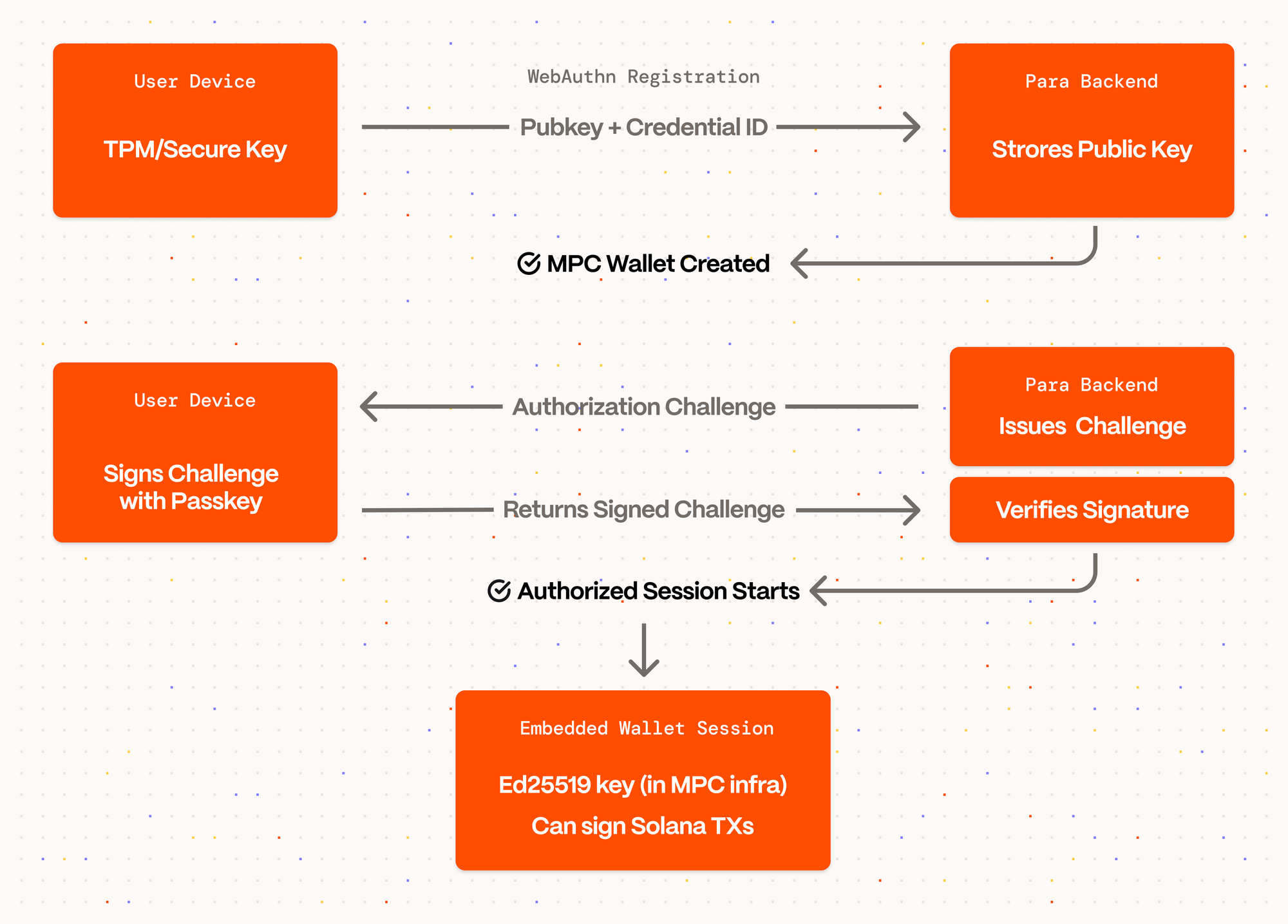
Here’s where our approach becomes important:
- The passkey itself isn’t used directly to sign Solana transactions (which must be Ed25519).
- Instead, the Para wallet SDK uses the passkey as an authorization primitive to unlock a session, which then grants scoped access to the Solana-compatible Ed25519 signing key used by the embedded wallet.
- This signing key lives within Para’s secure MPC-based key infrastructure, which is compatible with Solana’s signature requirements.
Effectively, the passkey authorizes, while the wallet key performs the signing. This unlocks sensitive operations such as sending transactions, accessing encrypted keys, and approving smart contract interactions. By separating identity from signing authority, we ensure that even high-stakes actions are protected by cryptographic authorization rather than just user login.
Para passkeys take this a step further, making it possible to embed wallets directly into apps without browser extensions or recovery phrases.
For Solana developers, Para UX translates into:
- Higher conversion during onboarding because wallets are embedded into your app
- No risk of loss of private keys or seed phrases
- Better UX and security while saying Solana-native
Why do passkeys matter for Solana Developers?
Passkeys are already live in apps like Xelio, which use them to onboard users into embedded wallets with zero friction via SMS. Other projects, like the SWIG Smart Wallet, are also adopting passkey-based flows for secure, app-native onboarding.
As more apps adopt embedded wallets with passkey-based access, we move closer to a universal wallet UX layer—one where users carry their identity and signing authority seamlessly between apps, devices, and sessions. This is especially important in ecosystems like Solana, where composability and app chaining are becoming the norm.
Passkeys are already being adopted across Web2
Major platforms like Google, Apple, and Meta now support passkeys for passwordless login, and many consumer apps are following suit. As passkeys become a default login method across the internet, Solana apps have a unique opportunity to catch up by using passkeys not just for authentication, but as a secure foundation for wallet access and transaction signing.
How to Add Passkey UX to Your Solana App
Integrating passkey-based wallets to your Solana app using Para’s wallet SDK takes less than five minutes.
For more in-depth instructions, head to the Para Docs.
Here’s how it works, step-by-step:
Prerequisites
Para API Key: Obtain your API key from the Para Developer Portal.
Create a env.local file in the project root and add your key:
NEXT_PUBLIC_PARA_API_KEY=your_para_api_key_hereIf you're not using Next.js, adjust based on your framework:
- For Vite, use:
VITE_PARA_API_KEY- For Node.js
reference process.env.PARA_API_KEY1. Initialize a Session with Para SDK
Start by wrapping your app in the ParaProvider and configuring the Para SDK on the frontend. This prepares the embedded wallet environment, allowing you to create or restore user sessions.
<ParaProvider
paraClientConfig={{
env: Environment.BETA, // or Environment.PROD
apiKey: YOUR_API_KEY,
}}
externalWalletConfig={{
appName: YOUR_APP_NAME,
wallets: ["PHANTOM","GLOW","BACKPACK"],
walletConnect: { projectId: YOUR_WALLET_CONNECT_PROJECT_ID },
solanaConnector: {
config: {
endpoint: ENDPOINT_FOR_SOLANA_CONNECTION,
chain: SOLANA_CHAIN,
},
},
}}
paraModalConfig={{
oAuthMethods: ["GOOGLE","TWITTER","TELEGRAM"]
authLayout: ["AUTH:FULL","EXTERNAL:FULL"]
recoverySecretStepEnabled: true
onRampTestMode: true
}}
>
{REST_OF_APP}
</ParaProvider>2. Use Helius for RPC + Solana Interaction
With the session active, you can now sign and send Solana transactions via Para’s SDK.
This signer exposes the standard signTransaction method compatible with Solana's @solana/web3.js API.
const connection = new Connection(HELIUS_RPC_URL);
const solanaSigner = new ParaSolanaWeb3Signer(para, Connection);
const tx = new Transaction().add(...);
const signedTx = await solanaSigner.signTransaction(transaction);
await connection.sendRawTransaction(signedTx.serialize());Leveraging Helius and Para gets you the UX of passkeys and Solana-native signing on-chain without ever exposing private keys or requiring browser extensions.
Check out Xelio for a real-world Solana app using passkeys and Para to streamline onboarding.
Solana signing out of the box
Passkeys on Solana offer more than passwordless login. They unlock a simpler, more secure way to onboard users into crypto wallets. With Para, developers get native access control, persistent sessions, and Ed25519 signing that works with Solana out of the box.
Learn more about passkeys on Solana in the Para docs and get started building with Para today.



